Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
Secure Login secures the underlying application with a 2-factor authentication: First, log in to the application as usual with your username and password. Only you know your password, so it is the first factor. The second factor is an authenticator that continually generates a PIN. Usually, it is an app on your smartphone or for example a Yubikey or hardware dongle, but in both cases, it is your non-shared hardware. This means that your identity will be verified by combining your access data and entering a valid PIN as part of the extended login.
Secure Login provides both ways of 2-factor authentication. To use an authenticator app, you have to pair the authenticator with Secure Login yourself. How this works is described in the section Secure Login Onboarding. If your organization uses hardware tokens, the administrator will do the onboarding process for you and you will receive the configured hardware token from him or her.
Secure Login hardware token usage
| Anchor | ||||
|---|---|---|---|---|
|
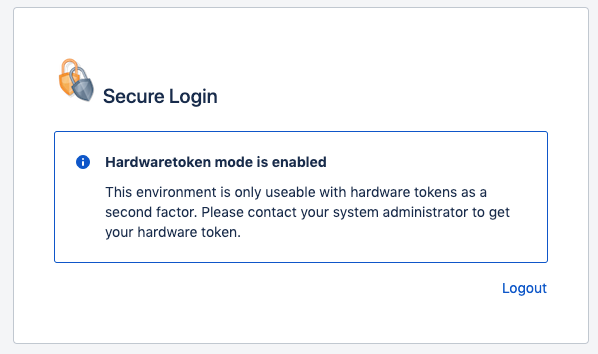
If your company only uses hardware tokens, you will receive the following screen if you have not yet assigned a hardware token. In the displayed screen the message can be different, because the system administrator can choose it as desired.
Secure Login Onboarding with secret key
| Anchor | ||||
|---|---|---|---|---|
|
Initial registration is required to set up your Secure Login profile, if your organization does not use hardware tokens.
Onboarding with secret key
You will need an authenticator app for your smartphone. Secure Login will provide you suggestions for suitable authenticator on the welcome dialog during the onboarding process below.
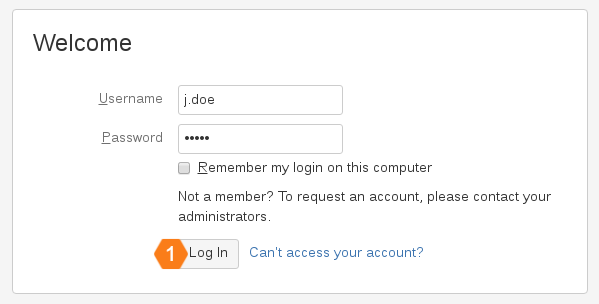
First, log in with your credentials as usual.
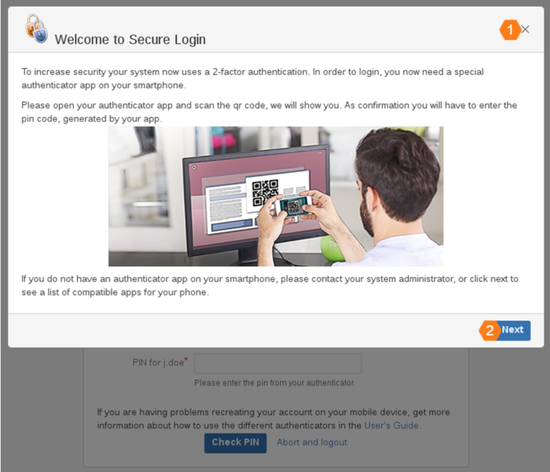
The welcome dialog will be displayed. Close this dialog to skip the instructions and continue with the onboarding process.
Or navigate through the instructions about Secure Login and our suggestions about suitable authenticator apps according to RFC 6238.
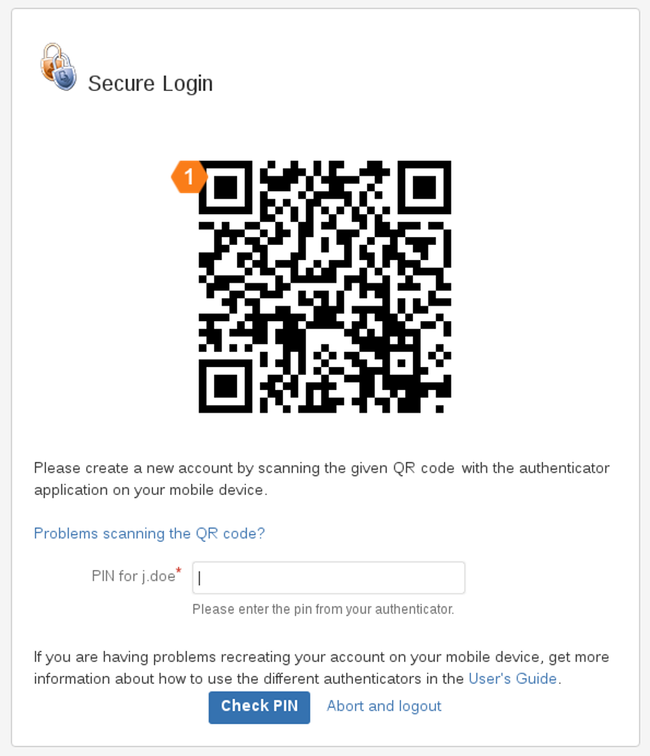
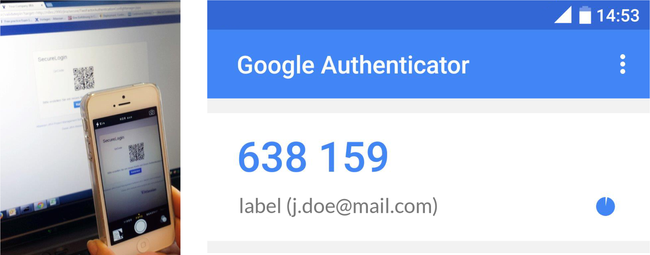
 Use your authenticator app and scan the QR code as shown in the left picture above. After you have scanned the QR code, the authenticator app periodically generates new PINs and displays them as shown in the right picture above.
Use your authenticator app and scan the QR code as shown in the left picture above. After you have scanned the QR code, the authenticator app periodically generates new PINs and displays them as shown in the right picture above.
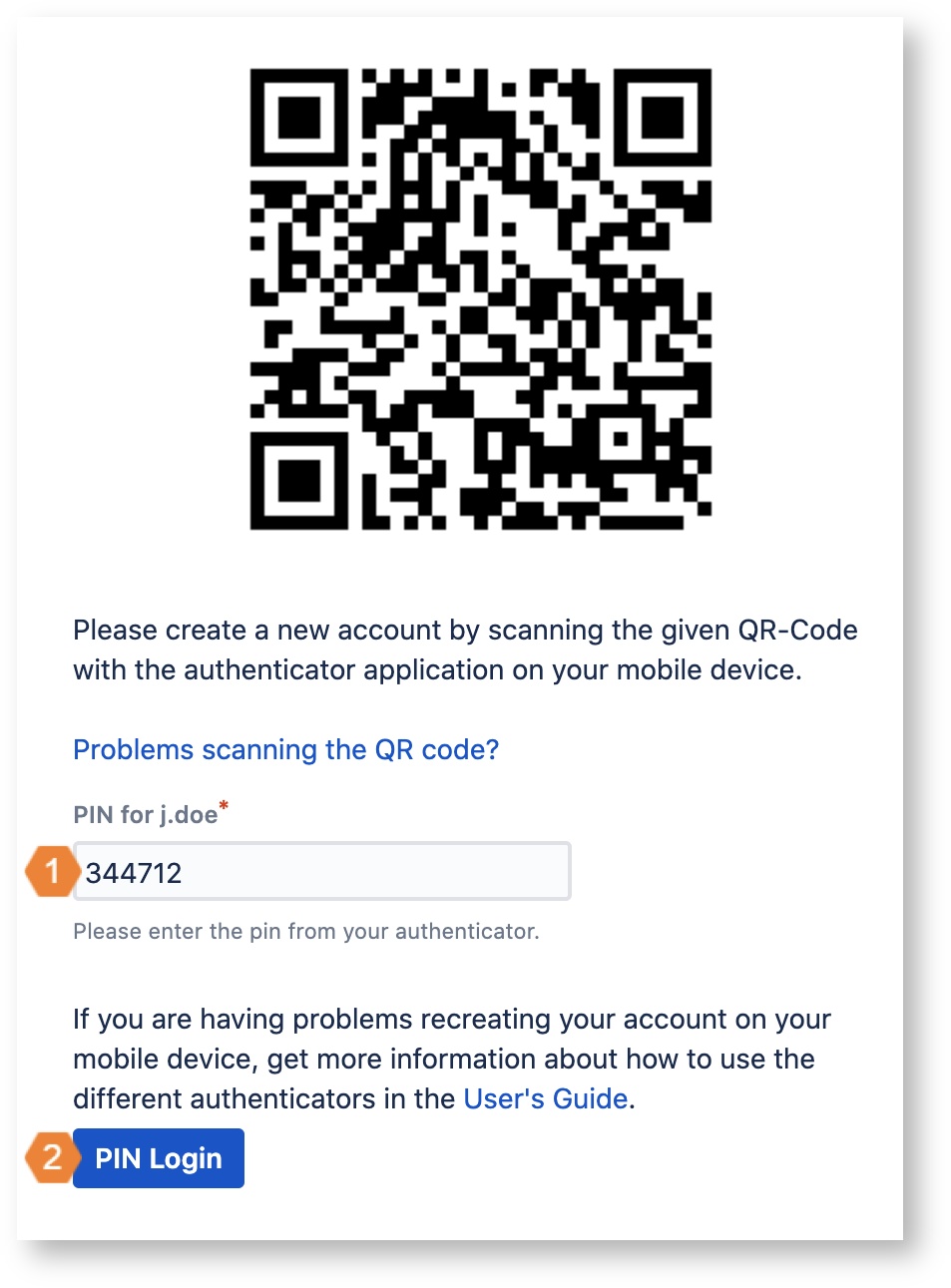
Use the PIN displayed in the authenticator app and enter it into the PIN input field of the onboarding dialog.
Click on Check PIN to complete the onboarding process.
Onboarding with WebAuthn/FIDO2
If your company allow to use WebAuthn/FIDO2 login, you can register a WebAuthn/FIDO2 device to set up your Secure Login profile.

 Enter a Device name to identify the device to register.
Enter a Device name to identify the device to register.
 Click Register device to complete the onboarding process.
Click Register device to complete the onboarding process.
Secure Login validation
After you have completed the onboarding or you received your hardware token, you need to enter the current valid PIN or use your WebAuthn/FIDO2 device for every time you log in again.
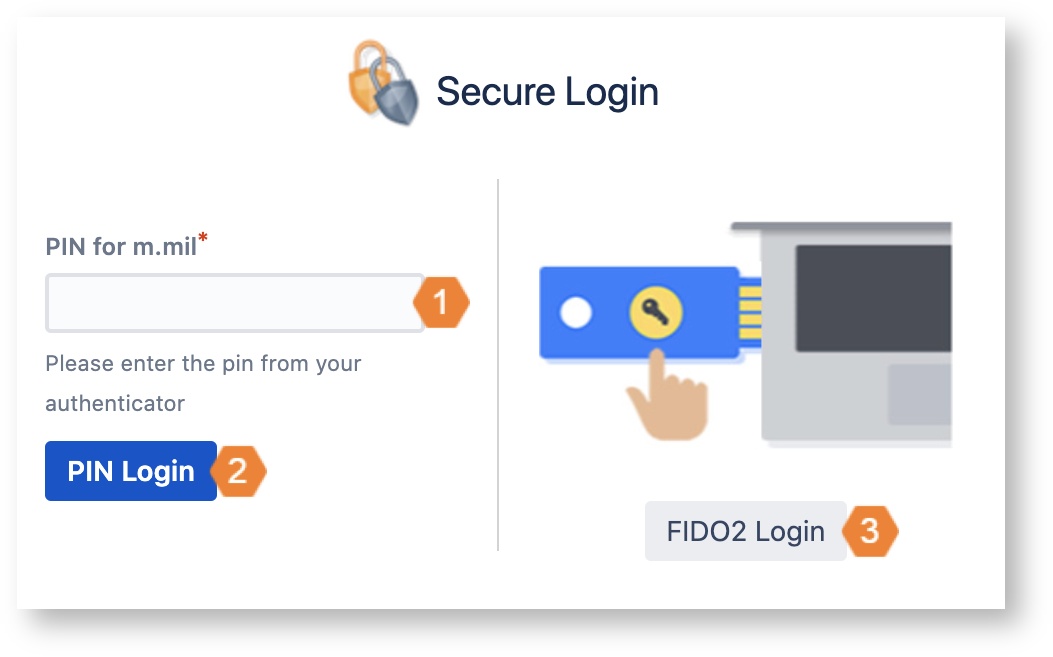
 Enter the currently displayed PIN in the input field.
Enter the currently displayed PIN in the input field.
 Click on Check PIN. If your PIN is valid, you'll be logged in.
Click on Check PIN. If your PIN is valid, you'll be logged in.
 Click on FIDO2 Login and follow the instructions. If your device is valid, you'll be logged in.
Click on FIDO2 Login and follow the instructions. If your device is valid, you'll be logged in.
Secure Login for Atlassian Mobile App
...
User Profile
| Anchor | ||||
|---|---|---|---|---|
|
In the Secure Login Profile you can view or reset your secret key. That allows you to link a new authenticator or reset your secret key independently of your system administrator.
Access your Secure Login Profile at...
| Expand | ||
|---|---|---|
| ||
|
| Expand | ||
|---|---|---|
| ||
|
| Expand | ||
|---|---|---|
| ||
|
| Expand | ||
|---|---|---|
| ||
|
Register another authenticator
If you want to use a different authenticator, log in and access your Secure Login profile as described in section User Profile.
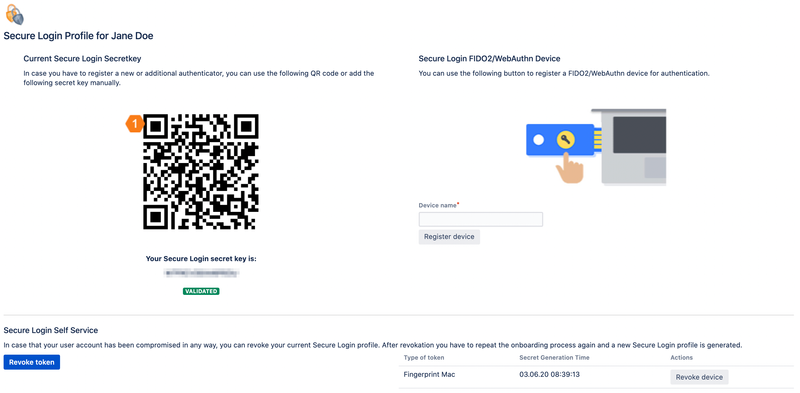
Scan the QR code with your desired authenticator app as you already know it from the onboarding process. Your new authenticator app now generates PINs for you.
| Note |
|---|
If you need to perform pairing because you want to use another smartphone for authentication, we recommend you to delete the account in the authenticator app on the previous smartphone to ensure that only you have access to the generated valid PINs. Alternatively, you can also revoke the token as described in section Revoke token and repeat the onboarding process with the authenticator app on your desired smartphone. |
Revoke token
| Anchor | ||||
|---|---|---|---|---|
|
If you suspect that your account may be compromised, your access token should be revoked. You can do this on your own in the Secure Login Profile, if you are using an authenticator app on your smartphone. If you are using a hardware token, your administrator have to revoke your token and configure your Secure Login Profile again.
To revoke your token by yourself, log in first and access your Secure Login profile as described in section User Profile.
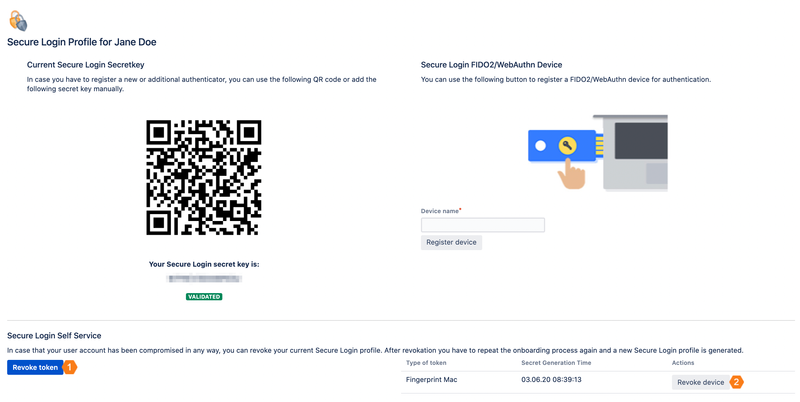
 Click on Revoke token. As soon as you leave the page, you will be prompted to repeat the onboarding process, if you have no further registration. A new secret key is generated for you.
Click on Revoke token. As soon as you leave the page, you will be prompted to repeat the onboarding process, if you have no further registration. A new secret key is generated for you.
 Click on Revoke device. As soon as you leave the page, you will be prompted to repeat the onboarding process, if you have no further registration.
Click on Revoke device. As soon as you leave the page, you will be prompted to repeat the onboarding process, if you have no further registration.
| Note |
|---|
If you have lost your authenticator and can no longer log in any longer, please contact your system administrator. He or she will be able to revoke the token for you. |
| Panel | ||||||
|---|---|---|---|---|---|---|
| ||||||
On this page:
|